Your computer has been compromised or hacked
Though surfing the world-wide-web, some users have viewed a popup information stating Your computer system has been compromised or hacked. Different consumers have noticed this concept on diverse browsers, including Chrome, Firefox, Edge, and so forth. Right after getting this warning concept, the influenced buyers scanned their computers with the antivirus put in on their devices but the antivirus did not discover any danger. If the antivirus danger report is distinct, what does this concept indicate? Is this concept serious or pretend? In this posting, we will see what the Your laptop or computer has been compromised or hacked message implies and what you should really do if you see this information on your laptop.

Your laptop or computer has been compromised or hacked
According to the responses of the influenced people, their internet browser refuses to near immediately after they receive the popup information. Also, a make contact with quantity is exhibited along with the warning information. When they contacted that amount, the guidance particular person questioned them for some income to correct the problem. On the other hand, some customers have also documented that after checking out a sure net web page, alternatively of the warning popup message, they listened to a voice indicating “Your Computer is hacked.”
Some end users were being also advised to give accessibility to their personal computers in buy to resolve the challenge. This is a spam and misleading concept. You really should overlook it otherwise, you will grow to be the prey of hackers. Furthermore, if you grant obtain to your computer system to the human being on the call, he/she may possibly steal the data saved on your laptop that may have sensitive information.
These types of sorts of warning messages normally display both a get in touch with amount or a url. We suggest you do not click on on the hyperlink displayed in this kind of styles of warning messages. If you do so, a virus or malware may possibly enter your technique and may perhaps start off sending your info to the hackers. Or, clicking on that url may well install a software on your technique. That plan may possibly incorporate a suspicious code. These kinds of types of destructive packages are designed to adjust the registry keys on a user’s computer system.
If you see a Your computer has been compromised or hacked warning message whilst surfing the world wide web, you should really acquire the adhering to actions straight away in get to safeguard your computer system from malware or virus an infection:
- Disconnect your Internet relationship
- Shut your web browser
- Scan your process with antimalware
- Update your web browser
- Eliminate unwanted extensions
- Delete your browser cache or reset your browser
- Uninstall the lately installed programs
- Operate SFC and DISM scans
Down below, we have described all these ways in depth.
1] Disconnect your World wide web link
Instantly disconnect your Internet connection to start with.
2] Close your web browser
The subsequent matter that you should do is to near your net browser. But according to the end users, the popup message may possibly prevent you from closing the website browser. If such a issue comes about to you, stick to the down below-mentioned techniques to close your world-wide-web browser:
- Push the Ctrl + Shift + Esc keys to start the Job Manager.
- When the Job Supervisor seems on your screen, pick the Processes tab.
- You will see your internet browser beneath the Applications area. Suitable-click on on your web browser and find Conclude Task.
If the previously mentioned strategy fails, pressure shut down your computer by pressing and holding the electrical power button and then change it on.
3] Scan your program with antimalware
If you have clicked on the connection provided in the warning information or if you have granted entry to your computer system to the individual on contact, there is a solid risk that your computer system has been contaminated by a virus. Run a full system antivirus scan.
Browse: How do you convey to if your personal computer has a virus?
4] Update your internet browser

Launch your website browser and near all the opened tabs if any.
Now update your web browser. It is advisable to generally use the hottest version of the software program in get to keep away from glitches. If you use the most up-to-date edition of the internet browser, the odds of receiving a virus or malware attack become much less.
Browse: Online Fraud in Cyber crime: Avoidance, Detection, Restoration
5] Clear away unwanted extensions

Now, the next phase is to take away undesirable extensions from your internet browser. Extensions make our operate a lot easier on a world-wide-web browser. Sometimes, extensions cause troubles. If you have clicked on the link shown in the warning information, it is doable that an extension is mounted on your browser with no your expertise. That’s why, it is essential to look at if there is any undesirable exten
sion installed on your browser. If you discover any undesirable extension or an extension that is installed on your world wide web browser without your understanding, take out it instantly.
Study: Malware Removal Manual & Equipment for Newbies.
6] Delete your browser cache or reset your browser
You should also delete your browsing record, together with the cookie and cache information. Press the Ctrl + Change + Delete keys to open up the Apparent Browsing Details window in your net browser. This shortcut is effective with most net browsers. When the Very clear Searching Knowledge window seems, find cookies, cache, and browsing history. In the time variety, pick out All Time. If you want to delete your saved passwords, you can also do that.
Alternatively, you might want to think about resetting your browser to default point out to be pretty secure.The steps to reset some preferred world-wide-web browsers are stated below:
- To reset or refresh Mozilla Firefox, open its options and go to “Help > Troubleshooting Information and facts.” Now, simply click on the Refresh Firefox button.
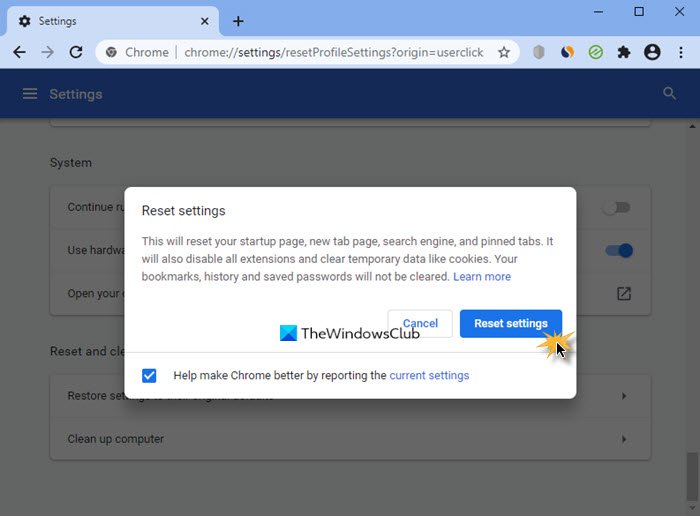
- To reset Google Chrome, open its options and go to Superior Settings. Now, simply click on the Restore configurations to their original defaults button.
- To reset Microsoft Edge, open its configurations and then click on the Reset Options choice on the still left pane.
7] Uninstall the recently installed courses
If you have known as the scammers or clicked on the website link shown in the warning message, the scammers may possibly have set up a application on your technique. Open the Apps & Functions page in Home windows 11/10 Configurations and see if there is any just lately put in system. If yes, uninstall it promptly. The adhering to actions will tutorial you on how to do that.

- Open Home windows 11/10 Options.
- Go to “Applications > Applications & Functions.”
- Type all the put in programs by date. For this, pick Day installed in the Sort by drop-down.
- See if there is any plan that is installed without having your information. If certainly, uninstall it.
8] Run SFC and DISM scans
It is also achievable that some of your method image data files are weakened due to malware or virus an infection. To check this, run an SFC scan. SFC stands for Program File Checker. It is an automated software formulated by Microsoft that checks for harmed or corrupted procedure picture data files and repairs them (if probable).
We also recommend you run a DISM scan on your method. The DISM or Deployment Image Servicing and Management is a command-line instrument. Like SFC, it also repairs the corrupted or damaged procedure graphic information. It is normally used when SFC fails to mend the procedure picture data files.
Examine: What to do soon after a Ransomware attack on your Windows laptop or computer?
What does it signify if your pc is compromised?
A compromised personal computer is a laptop or computer, the confidentiality of which is adversely impacted, possibly intentionally or unintentionally. The phrase Compromised computer system is typically utilized for hacked computer systems. There are a lot of methods by which hackers can hack your process. The most common way is the phishing endeavor. The phishing makes an attempt are ordinarily accomplished by sending an electronic mail to the user with some suspicious back links. When a consumer clicks on these backlinks, he will be redirected to the web site that appears just the exact as the formal site. These internet websites trick customers and they enter their confidential information although signing in. In this way, hackers steal the confidential details of the end users.
Whilst browsing the internet by using your web browser, some of you might have observed the messages comparable to the subsequent kinds immediately after viewing some specific sites:
- Your laptop or computer could be at chance. Run a free antivirus scan to defend your computer system.
- Virus detected. Operate a cost-free antivirus scan to take away the virus from your computer system.
These kinds of sorts of internet websites are malicious internet websites. Clicking on any of the backlinks on these kinds of internet sites installs malware on the user’s computer. Soon after the malware is set up, a destructive code is executed on his/her computer and the hacker is in a position to steal the data from the contaminated computer system. Some malware are also capable of changing the registry keys on a Windows pc.
Tip: Secure oneself, prevent on the internet scams and know when to have confidence in a web-site!
Does Microsoft contact you about your computer being hacked?
Hold in thoughts that neither Microsoft nor its partners connect with you for your computer system stability difficulties. You need to have to study how to identify frauds that fraudulently use the Microsoft name. The motive of these calls is to steal the confidential info from the user’s personal computer so that they could use it for blackmailing applications. The individual on phone might also inquire to obtain your laptop by installing a specific software. If you grant him/her obtain to your computer system, he/she may perhaps execute a malicious code on your method or completely lock your laptop. After that, the hacker will inquire you for a specified amount of money of cash to unlock your laptop.
Hope this helps.
Read subsequent: Command and Control Cyberattacks: How to Recognize and Stop them?